Smuggling arbitrary data through an emoji 😀󠄵󠅢󠅢󠅕󠅥󠅢󠄣󠄢
💀󠅀󠅟󠅧󠅞󠅕󠅔󠄐󠅒󠅩󠄐󠄵󠅢󠅢󠅕󠅥󠅢󠄣󠄢
This Hacker News comment by GuB-42 intrigued me :
With ZWJ (Zero Width Joiner) sequences you could in theory encode an unlimited amount of data in a single emoji.Is it really possible to encode arbitrary data in a single emoji?
tl;dr: yes, although I found an approach without ZWJ. In fact, you can encode data in any unicode character. This sentence has a hidden message󠅟󠅘󠄐󠅝󠅩󠄜󠄐󠅩󠅟󠅥󠄐󠅖󠅟󠅥󠅞󠅔󠄐󠅤󠅘󠅕󠄐󠅘󠅙󠅔󠅔󠅕󠅞󠄐󠅝󠅕󠅣󠅣󠅑󠅗󠅕󠄐󠅙󠅞󠄐󠅤󠅘󠅕󠄐󠅤󠅕󠅨󠅤󠄑.
https://paulbutler.org/2025/smuggling-arbitrary-data-through-an-emoji/
(Try pasting it into this decoder)
https://emoji.paulbutler.org/?mode=decode
How long it take to CRACK your password ??
DFShell - The Best Forwarded Shell
2 hrs ago 8:30 AM | Post sponsored by FaradaySEC | Multiuser Pentest Environment Zion3R
██████╗ ███████╗███████╗██╗ ██╗███████╗██╗ ██╗
██╔══██╗██╔════╝██╔════╝██║ ██║███╔═══╝██║ ██║
██║ ██║█████╗ ███████╗███████║█████╗ ██║ ██║
██║ ██║██╔══╝ ╚════██║██╔══██║██╔══╝ ██║ ██║
██████╔╝██║ ███████║██║ ██║███████╗████████╗███████╗
╚═════╝ ╚═╝ ╚══════╝╚═╝ ╚═╝╚══════╝╚══════╝╚══════╝
D3Ext's Forwarded Shell it's a python3 script which use mkfifo to simulate a shell into the victim machine. It creates a hidden directory in /dev/shm/.fs/ and there are stored the fifos. You can even have a tty over a webshell.
In case you want a good webshell with code obfuscation, login panel and more functions you have this webshell (scripted by me), you can change the username and the password at the top of the file, it also have a little protection in case of beeing discovered because if the webshell is accessed from localhost it gives a 404 status code
Why you should use DFShell?
To use other forwarded shells you have to edit the script to change the url and the parameter of the webshell, but DFShell use parameters to quickly pass the arguments to the script (-u/--url and -p/--parameter), the script have a pretty output with colors, you also have custom commands to upload and download files from the target, do port and host discovery, and it deletes the files created on the victim if you press Ctrl + C or simply exit from the shell.
If you change the actual user from webshell (or anything get unstable) then execute: 'sh'
Flipper Zero
Flipper Zero is a portable multi-tool for pentesters and geeks in a toy-like body. It loves hacking digital stuff, such as radio protocols, access control systems, hardware and more. It's fully open-source and customizable, so you can extend it in whatever way you like.
Exploits of the week
Online Student Enrollment System 1.0 - Cross-Site Request Forgery (Add Student)
Code Blocks 20.03 - Denial Of Service (PoC)
WebPort 1.19.1 - 'setup' Reflected Cross-Site Scripting
WebPort 1.19.1 - Cross Site Scripting
Frigate 2.02 - Denial Of Service (PoC)
Responsive Online Blog 1.0 - 'id' SQL Injection
Trend Micro Web Security - Remote Code Execution
Lansweeper 7.2 Default Account / Remote Code Execution
Student Enrollment 1.0 - Remote Code Execution
FileRun CVE-2019-12905 - Cross Site Scripting
pentest test hack vul
Accounts
8,165,160,541
Leaks
810
Leaked accounts per day
879,875
Is someone spying on you?
Everyday personal data is stolen in criminal cyber attacks. A large part of the stolen information is subsequently made public on Internet databases, where it serves as the starting point for other illegal activities.
With the HPI Identity Leak Checker, it is possible to check whether your email address, along with other personal data (e.g. telephone number, date of birth or address), has been made public on the Internet where it can be misused for malicious purposes.
J'avais besoin d'un double de mon badge d'immeuble alors je l'ai fait moi même ^_^
Voici comment faire ;-)
Matériel :
- NFC ACR122U RFID Contactless Smart Reader & Writer/USB + 5X Mifare IC Card JK
- UID Changeable by Phone M1 card Sector 0 block0 Rewritable 1K card S50 1 10pcs
Installation
sudo apt install libnfc-dev libnfc5 libnfc-bin libusb-dev make gcc unzip automake
Installation de mfoc
wget -O mfoc-master.zip https://github.com/nfc-tools/mfoc/archive/master.zip
unzip mfoc-master.zip
rm mfoc-master.zip
cd mfoc-master/
autoreconf -vis
./configure
make
sudo make install
cd ..
Vérification du fonctionnement du lecteur :
nfc-list
nfc-list uses libnfc 1.7.0
NFC device: ACS / ACR122U PICC Interface opened
Pour l'erreur :
error libnfc.driver.acr122_usb Unable to claim USB interface (Device or resource busy)
nfc-list: ERROR: Unable to open NFC device: acr122_usb:003:00
La solution est :
sudo modprobe -r pn533-usb pn533 nfc
sudo nano /etc/modprobe.d/blacklist-libnfc.conf
et y mettre ajouter :
blacklist pn533_usb
blacklist pn533
blacklist usb
Installation de mfcuk pour choper les clés
Edit, version officielle : https://github.com/nfc-tools/mfcuk/archive/master.zip
version la plus récente : https://github.com/DrSchottky/mfcuk/archive/master.zip
wget -O mfcuk-master.zip https://github.com/DrSchottky/mfcuk/archive/master.zip
unzip mfcuk-master.zip
rm mfcuk-master.zip
cd mfcuk-master/
autoreconf -vfi
./configure
Dans src/mfcukfinger.c il y a un chemin relatif au dossier data --
Donc on change ça
sed -i "s#./data/tmpls#/usr/share/mfcuk/data/tmpls#" src/mfcuk_finger.c
sudo mkdir -p /usr/share/mfcuk/data/
sudo cp -r src/data/* /usr/share/mfcuk/data/
make
sudo make install
cd ..
Et maintenant, le hack :-)
On place le badge à copier sur le lecteur et cherche la clé
Pour les badges Urmet, on teste une copie avec la clé 8829da9daf76
mfoc -k 8829da9daf76 -O badge.dmp
Si ça marche pas, on brut force.
Comme ça peut prendre des 10ène de minutes voir des heures,
on envoi le résultat vers log_mfcuk et on met ça en tâche de font
Attention au « -v ». Voir plus bas
mfcuk -C -R 0:A -s 250 -S 250 -v 3 > log_mfcuk&
pour voir où en est le log :
tail -f log_mfcuk
à la fin on doit avoir un truc du genre :
INFO: block 3 recovered KEY: XXXXXXXXXXXX
On peut aussi changer la verbose ( -v ) de mfcuk si le log est trop gros
Rappel pour killer un process :
pgrep mfcuk
On note le pid
kill -15 <pid de mfcuk>
On dump le badge
mfoc -k XXXXXXXXXXXX -O badge.dmp
On remplace le badge par une carte vierge
On dump de la carte
mfoc -P 500 -O new_carte.dmp
Et on fini par copier le tout sur la carte
nfc-mfclassic W a badge.dmp new_carte.dmp
Il ne reste plus qu'à tester la carte
:-)
Sources :
https://zozs.se/2014/08/18/acr122u-mfcuk-mfoc-cracking-mifare-classic-on-arch-linux/
http://www.latelierdugeek.fr/2015/07/17/dupliquer-contenu-puce-rfid-mifare-classic/
https://geekz0ne.fr/wiki/doku.php?id=modifier_informations_badges_selecta
Ixeygrek ( merci ;-) )
Quelques clés :
bticino : 021209197591
urmet : 8829da9daf76
ALARON BLARON : 414C41524F4E
generique : D3F7D3F7D3F7
Intratone : 484558414354
Comelit : 4A6352684677
https://github.com/iceman1001/proxmark3
https://github.com/iceman1001/proxmark3/blob/master/client/default_keys.dic
C’est maintenant que commence votre droit d’être à l’abri du piratage informatique.
Firefox Monitor met à votre disposition des outils pour conserver vos informations personnelles en toute sécurité. Découvrez quelles sont les données personnelles accessibles aux cybercriminels et apprenez à vous protéger.
Voyez si vous avez été impliqué dans une fuite de données.
L’adresse électronique doit être valide.
MOTEUR DE RECHERCHE DES FAILLES ET TOOLS
This is a simple place where you can download crackmes to improve your reverse engineering skills. If you want to submit a crackme or a solution to one of them, you must register. But before that, I strongly recommend you to read the FAQ
Number of users:
1500
Number of crackmes:
3016
Number of solutions:
4206
Inj3ct0r is the ultimate database of exploits and vulnerabilities and a great resource for vulnerability researchers and security professionals.
Our aim is to collect exploits from submittals and various mailing lists and concentrate them in one, easy-to-navigate database.
This was written solely for educational purposes. Use it at your own risk. The author will be not responsible for any damage. // r0073r
0day.today Available within TOR at http://mvfjfugdwgc5uwho.onion
Links of malware hack check tools :
- Loki
- phpscanner
- php-malware-finder
- php-malware-scanner
- Yasca
- acunetix
- RIPS-scanner
- nikto2
- phpsecaudit
- sectools
- phpsec
Loki
Simple IOC Scanner
Scanner for Simple Indicators of Compromise
phpscanner
PHP scanner written in Python for identifying PHP backdoors and php malicious code. This tool is mainly reusing below mentioned tools. To use this tool, you need to install yara library for Python from the source.
php-malware-finder
Does its very best to detect obfuscated/dodgy code as well as files using PHP functions often used in malwares/webshells. Detection is performed by crawling the filesystem and testing files against a set of YARA rules.
php-malware-scanner
Scans the current working directory and display results with the score greater than the given value. Released under the MIT license.
Yasca (GitHub)
an open source program which looks for security vulnerabilities, code-quality, performance, and conformance.
acunetix Web Security Scanner
Acunetix WVS automatically checks your web applications for SQL Injection, XSS & other web vulnerabilities.
RIPS
A static source code analyser for vulnerabilities in PHP .scripts
nikto2
an open source web server scanner which performs comprehensive tests against web servers for multiple items, including potentially dangerous files/program.
ClamAV extension for PHP (php-clamav) - a fork of the php-clamavlib project allows to incorporate virus scanning features in your PHP scripts.
Older projects: securityscanner, phpsecaudit.
Check also the following security websites:
sectools.org
phpsec.org PHP Security Consortium
Founded in January 2005, the PHP Security Consortium (PHPSC) is an international group of PHP experts dedicated to promoting secure programming practices within the PHP community. Members of the PHPSC seek to educate PHP developers about security through a variety of resources, including documentation, tools, and standards.Le chercheur en sécurité Xudong Zheng a publié un article très intéressant sur les noms de domaine forgés en punycode avec des caractères exotiques, ce qui permet de régler le problème de l'internationalisation des noms de domaine dans d'autres alphabets.
Ça part d'un bon sentiment, mais comme toujours, il y a quelques faiblesses dans le truc. En effet, niveau sécurité c'est problématique, car certains caractères ASCII sont difficiles à discerner d'autres caractères plus courants. Par exemple, si vous enregistrez le nom de domaine "xn--pple-43d.com", celui-ci s'affichera dans votre navigateur comme ceci : "аpple.com". Ça ne se voit pas au premier coup d'oeil, mais ce que vous pensez être le "a" d'Apple (en ASCII : U+0061) est en fait le caractère cyrillique "а" (Code ASCII : U+0430).
Cette technique dont j'ai déjà parlée sur ce site, utilisée principalement dans des attaques de type phishing est connue sous le nom d'attaque homographique.
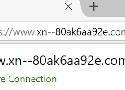
Heureusement, les navigateurs récents limitent ces attaques lorsqu'ils détectent des mélanges entre des caractères classiques et des caractères internationaux. Mais que ce soit Chrome, Firefox ou Opera, tous échouent lorsque l'intégralité du nom de domaine contient uniquement des caractères ASCII internationaux. Par exemple le nom de domaine "аpple.com" qui en réalité est enregistré sous le nom "xn--80ak6aa92e.com" arrive à contourner la protection en utilisant uniquement des caractères cyrilliques.
Vous pouvez faire le test vous-même via cette URL.
https://www.аррӏе.com/
Entrez dans le champ d'URL :
about:configPuis cherchez la clé :
network.IDN_show_punycodeEt mettez là à TRUE.
Ainsi, les noms de domaines exotiques s'afficheront au format punycode, ce qui vous évitera de tomber dans le panneau.
Autrement, en cas de doute, ce que vous pouvez faire c'est de retaper vous-même l'URL.
ABOUT
hackmud is a cyberpunk themed text-based hacking simulator for intel-compatible personal home computers. Get lost in a deep and complex world full of challenging puzzles.
Find the source of your leaks
There are currently 1,976,046,540 accounts in our database.